Note
This article was last updated on 01/30/2025 for readability and updated URLs
This short article was actually written last year but never published because Microsoft started applying Mark of the Web to virtual disk formats including ISO files in November. At the time, I didn’t feel it was necessary anymore…
1) We are finally propagating MotW to Virtual Disk containers! For example, when you download and mount an ISO from the Internet, applications that query the zone of files inside of that ISO will receive the zone of the ISO itself. 3/7
— Bill Demirkapi (@BillDemirkapi) November 8, 2022
But this week, there’s been a renewed interest in this thanks to The DFIR Report’s article detailing a compromise from September, prior to the patches being released. I was a little confused when Justin shared this because I jumped straight to the summary… so I assumed there was some bypass that wasn’t detailed :-/
New @TheDFIRReport https://t.co/fmca06oNda
— Justin Elze (@HackingLZ) April 3, 2023
Since it may still be relevant for someone out there (though not entirely necessary anymore), I’ve decided to go ahead and publish it anyway.
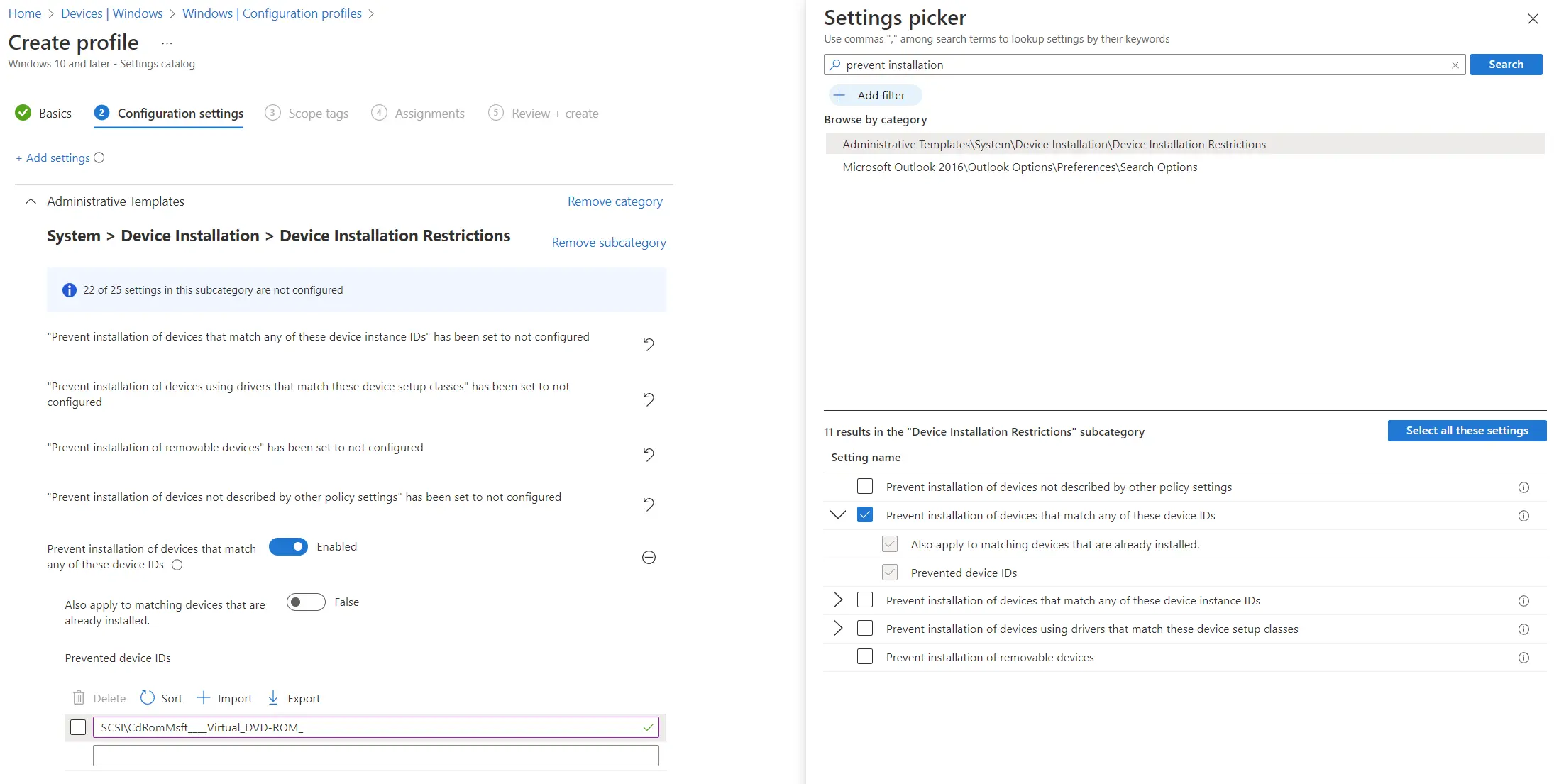
In case you missed it last year, Rob Fuller did some great research on ways to prevent ISO files from being mounted, and I thought it might be helpful to show the various ways we can do this using Intune :)
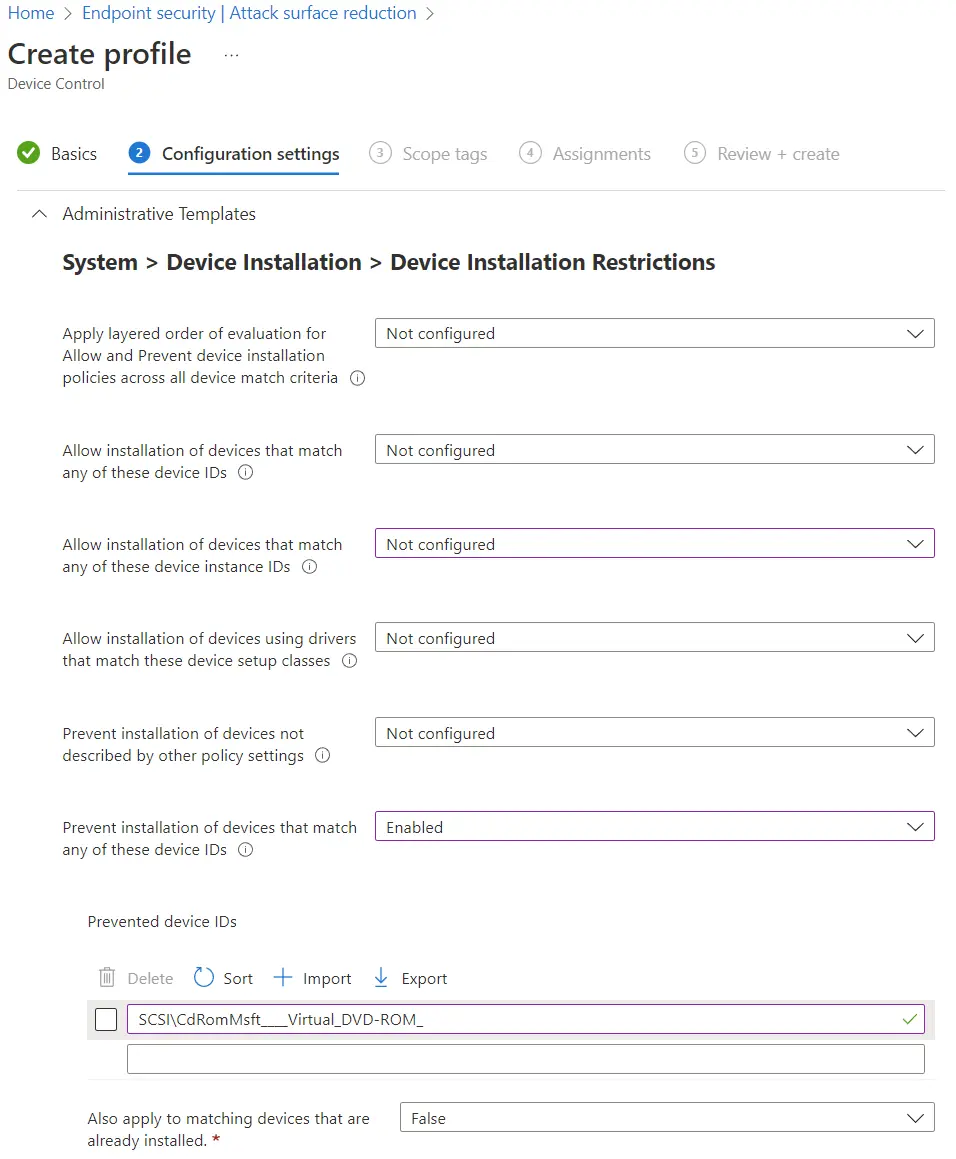
Rob mentioned using Group Policy, and we could definitely use Administrative Template profiles with the same controls. Alternatively, we could use Settings Catalog or using a Device Control profile under Endpoint security - Attack surface reduction.
Here are some screenshots to hopefully help folks see where / how we would implement these policies. The value that we use in the policy is:
1SCSI\CdRomMsft____Virtual_DVD-ROM_
Administrative Templates profile
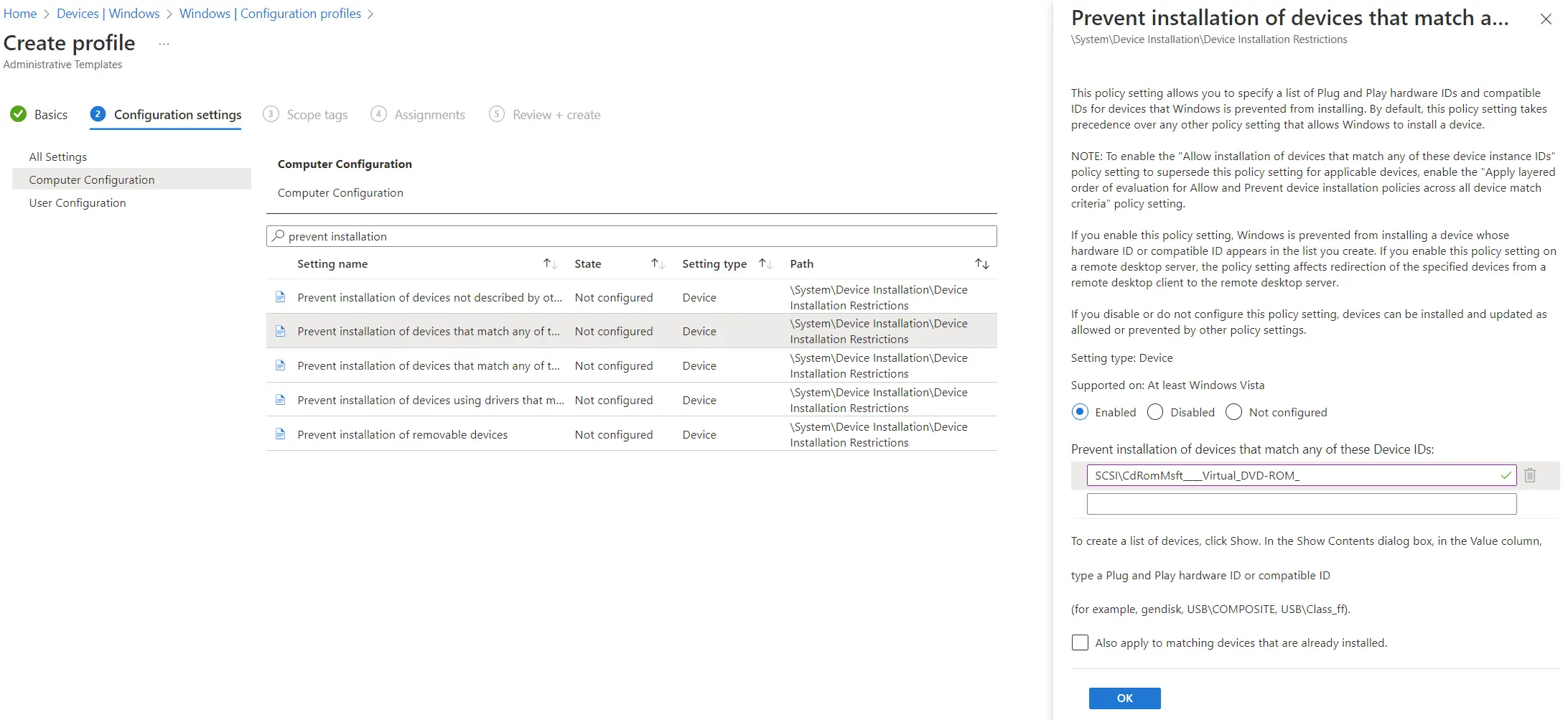
Settings Catalog
Device Control profile