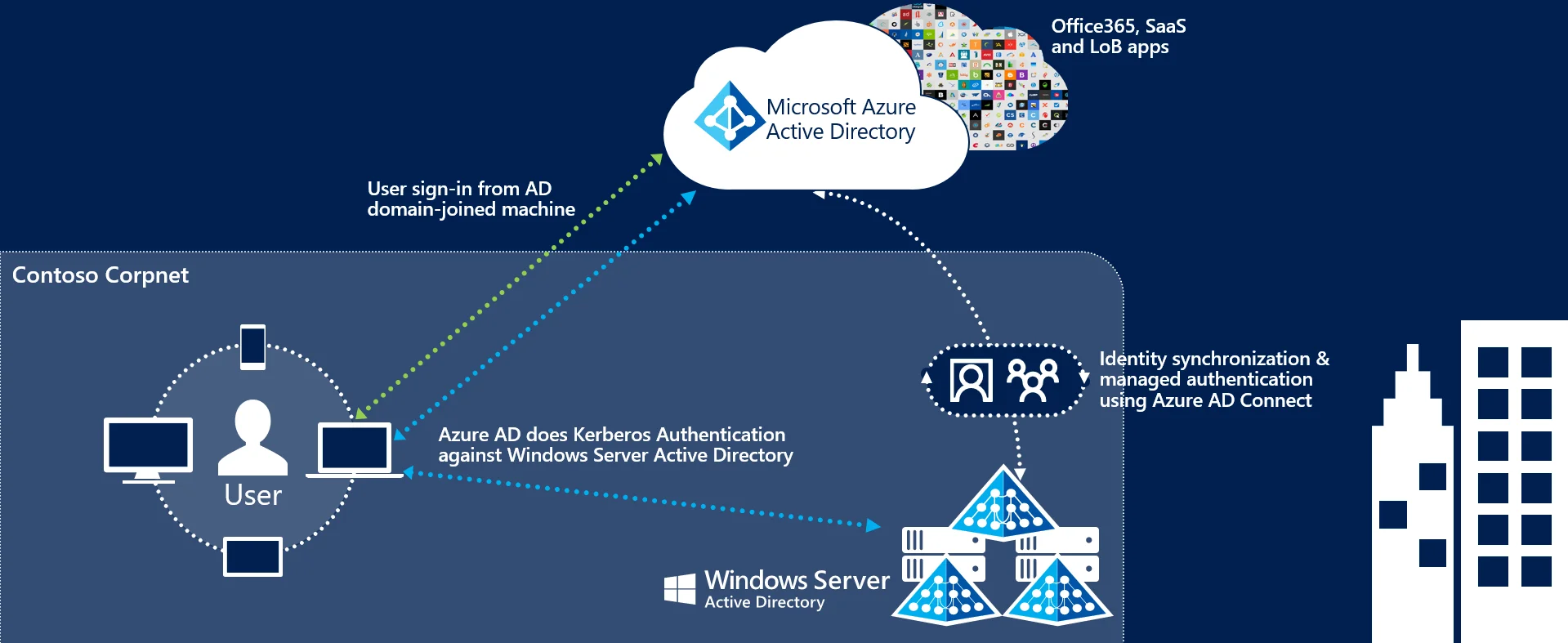
This post provides everything you need to ensure Advanced Auditing is fully configured and auditing everything we possibly can for both existing and new users. I recently shared guidance for this via social media (see below), and it felt like a perfect time to revisit my previous posts and combine everything into one comprehensive guide :)
You likely aren't collecting all available events to the Unified Audit Log
First, not all events are enabled or retained optimally. Consider creating this policy in the Purview portal (leave users and record types blank to collect everything).
Retention is based on license... pic.twitter.com/IEKKfrkpI8

👮 Restricted Management Admin Units (RMAU) in #EntraID
Hackers HATE This Hidden Entra ID Feature Most Admins Never Use@NathanMcNulty breaks it down for us 👇
🎧 Get the full podcast episode at https://t.co/gnvH23WorW pic.twitter.com/nxBwCQ6BwS
— Merill Fernando (@merill) March 29, 2025 I recently had a chance to discuss Restricted Management Administrative Units (RMAUs) with Merill, and one of my favorite uses for these is to protect groups that are used in Conditional Access policies so they aren’t accidentally modified or deleted. I’m also a big fan of using Access Packages to control membership of these groups for things like exclusions from geofencing policies, user action policies, blocking policies, etc.